We are living in a digital world, and wireless network feasibility is an immensely crucial part of it. Hence, the rise of Wi-Fi technology is at an all-time high; with an increasing number of wireless devices, our homes, public spaces, and workplaces are becoming more interconnected. This comes with its share of risk, as it creates room for cybercriminals to get unauthorized access to sensitive data. Inevitability security protocols were needed to safeguard your Wi-Fi usage.
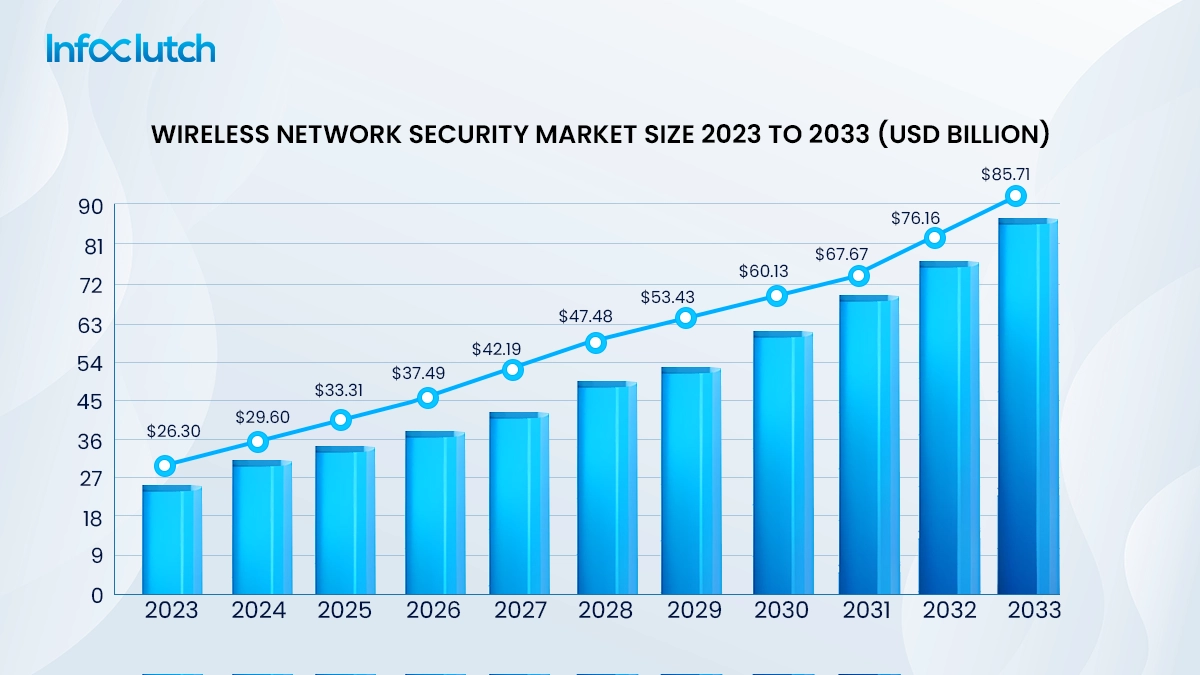
This brings us to the critical component of network security, which is WEP, WPA, different types of WPA2 and WPA3.From time to time, all of these have and keep on protecting wireless networks from unauthorized access and breaches to preserve integrity and confidentiality and prevent data theft. Its high demand is a significant contributor to the global wireless network security market, which is anticipated to reach a valuation of 85.71 billion.
In What Ways WI-FI Security Works?
Learn how your Wi-Fi network protects against data loss, interception, unapproved access, and spoofing. Here is a brief rundown of how it works.
- Encryption Data: This is the basic foundation of Wi-Fi security. First, it authenticates the user. The Wi-Fi access point will encode data transmitted between it and the device in a way that an unwelcome third party won’t be able to decode it. The information will be available only for the device with the correct encryption key.
- Network Type: Depending upon different networks, the Wi-Fi security differs, irrespective of whether it is home, public Wi-Fi network, or business. Businesses and homes have robust security measures, such as different types of WAP2 and WAP3 security protocols, as their work involves more sensitive data. Then again, the public Wi-Fi network might not need security measures; users have to employ their security measures, such as VPNs.
- Authentication: It is the general form with a pre-shared key (PSK); Wi-Fi security involves validating the identities of the devices trying to access a network with a simple access code. For enterprise Wi-Fi deployments, it’s not adequate. Corporate access credentials with user identity validation and relevant device certificates are required to onboard users and their IT devices onto a secure enterprise network.
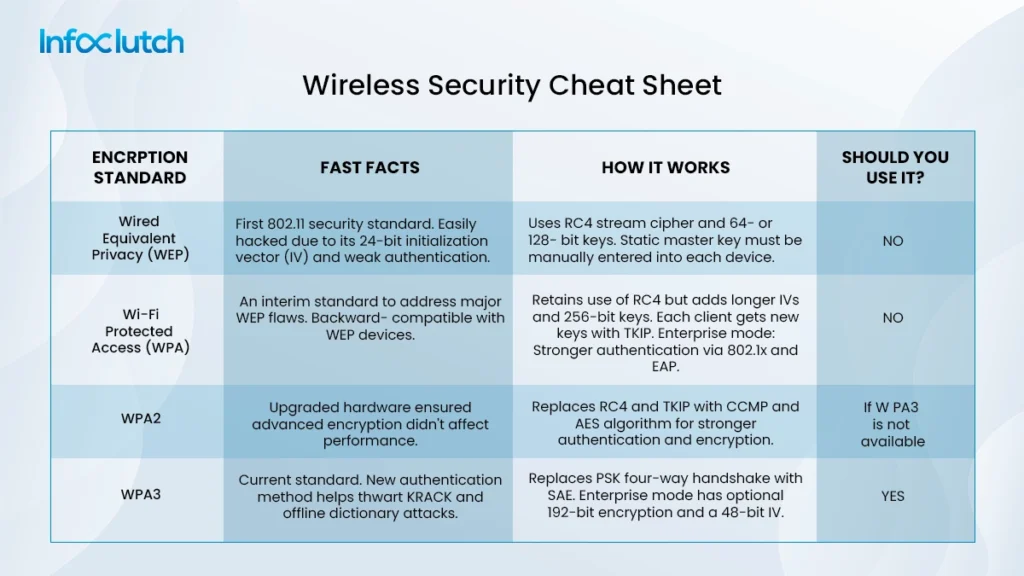
- Wi-Fi Security Protocols: Wi-Fi security protocol depends upon how the encryption is applied. The prevalent security protocols are WEP, WPA, WPA2, and WPA3. However, WEP and WPA were used previously, and they are older, outdated models which showcased significant security weaknesses. Presently, the most up-to-date and secure models are WPA2 and WPA3.
What are the Four types of Wireless Security Protocols?
94% of the companies utilize Wi-Fi security protocols, and most of them come along with the ability to enable one of the following wireless encryption standards:
- Wired Equivalent Privacy (WEP)
- Wi-Fi Protected Access (WPA)
- WPA2
- WPA3
What is WEP?
In 1997, Wired Equivalent Privacy (WEP) was the first wireless protection, with the goal of encrypting data. In case the wireless data is intercepted, it won’t be available in a recognizable format because of the encryption. However, the system registered for wireless protection, will be intimidated about the decrypt.
WEP encodes traffic using 64-128-bit key in hexadecimal. It’s a static key; therefore, regardless of the device, it is encrypted using a single key. Allowing computers to share coded messages from intruders.
The most crucial goal for WEP is to prevent middle-man-attack, which it was able to do for some time. Despite several revisions of protocol and increased key size, numerous security flaws were discovered in WEP over time. That’s why WEP security is considered obsolete; it is only in use under certain circumstances, such as when the authorities haven’t changed the default security of the wireless routers or the device configuration cannot support the new encryption method like WPA.
What Is WPA?
Wi-Fi protected access, otherwise known as WPA, was introduced in the year 2003. It had similarities with WEP but additionally offered improvements with the security keys and the process of offering authorization. WPA provides a temporal key integrity protocol (TKIP), which dynamically changes the key according to the particular system using the key. The primary purpose of TKIP is to prevent intruders from creating their own encryption key, which will be similar to the one used by the secured network. The key used in WPA is 256-bit, and it significantly increased over the 64-bit and 128-bit keys used for WEP.
Unfortunately, even with such strides of improvement, the TKIP encryption standard was later replaced by an advanced Encryption Standard. As the elements of WAP were exploited and, it led to different types of WPA2.
However, you might still hear the term “WPA key” while a discussion for WPA is taking place. A WPA key is a password for the wireless network. It is the password you can gather from someone who runs the network. Sometimes, the password is printed on a wireless router.
What is WPA2?
WPA2 came into existence in 2004, an upgraded version of WPA. The WPA2 is created based on a robust security network. It was created to address shifting network needs, which will counter the older encryption methods.
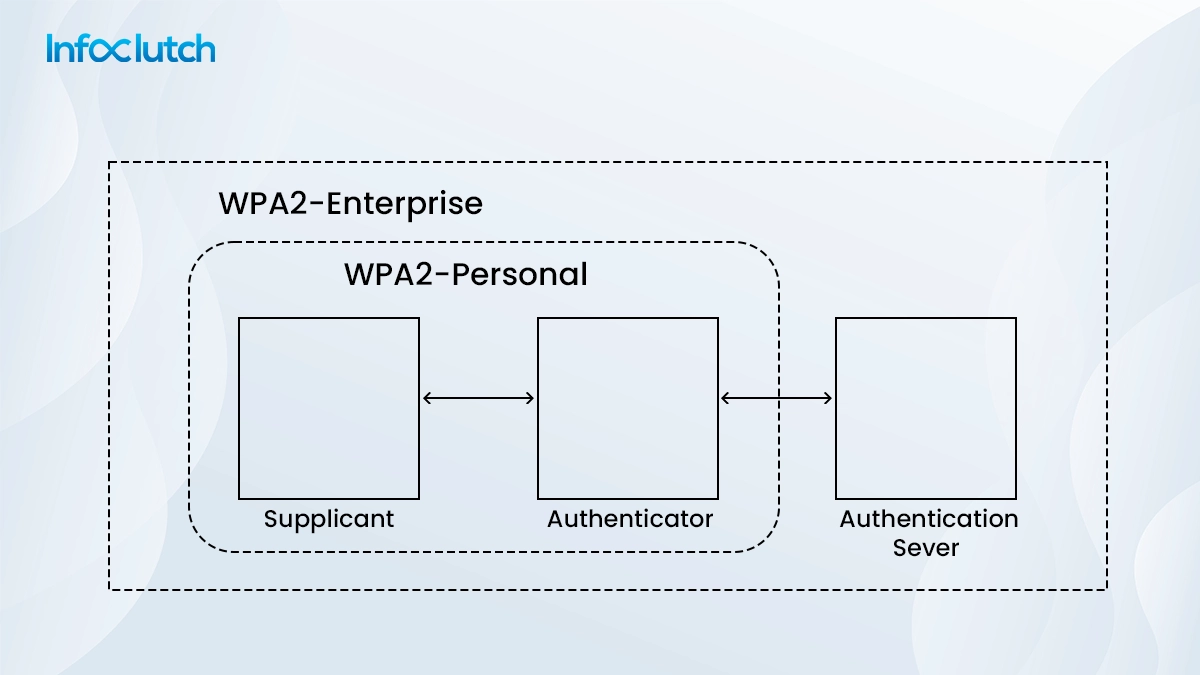
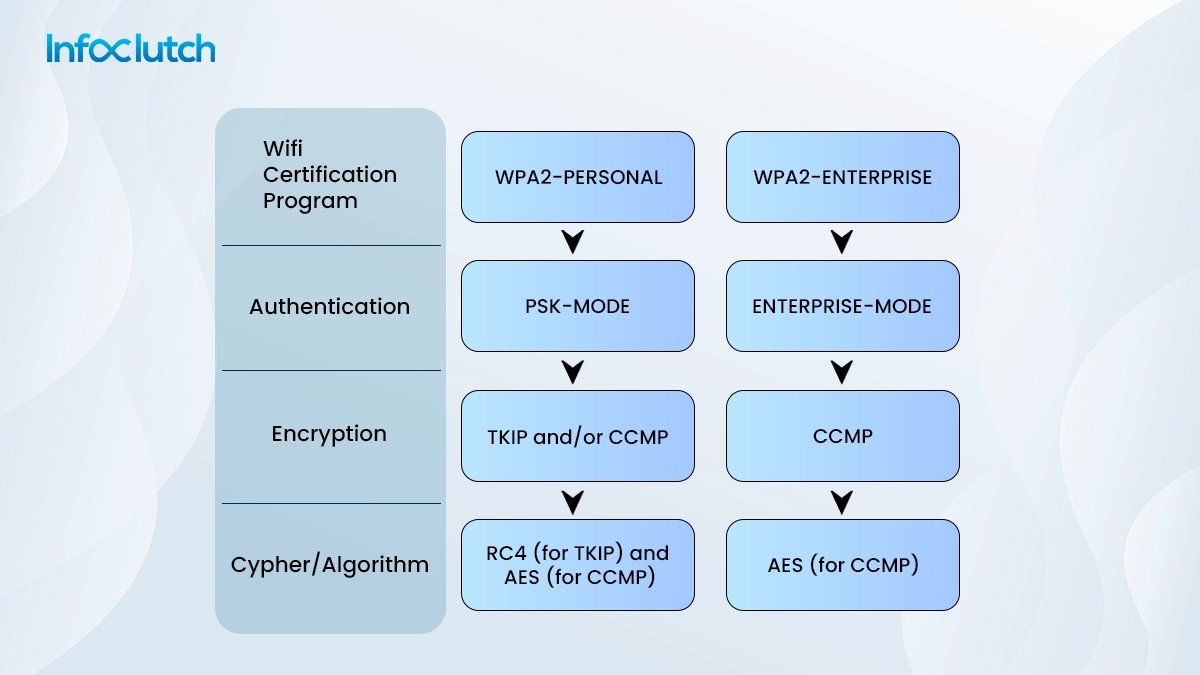
There are two different types of WPA2 protocol that are leveraged today to provide varied levels of security; they are WPA2-PSK/ and WPA2-ENT.
- WAP2-ENT was created for business purposes and uses 802.1X for enterprise-grade authentication.
- WAP2-PSK is created to use for home and uses pre-shared-keys (PSK)
However, many organizations still need clarification on which one will be more secure for their work. Over here, we will inform you about different types of WPA2, their use cases, and security.
What do you need to know About WAP2 Authentication?
WPA2 is supreme wireless security as it utilizes an advanced encryption system (AES) that is better than the Temporal key integrity protocol (TKIP). It has a couple of different authentication protocols. Enterprise (ENT) and Pre-shared-key (PSK) are used similarly for businesses and at home. The authentication protocol comes into the picture when a user connects and re-connects to the network.
WPA2-PSK (Wi-Fi Protected Access-Pre-Shared Key)
For every wireless client, the encryption key is generated with a passphrase, and the network service set identifier (SSID) is used by the TKIP protocol. Furthermore, WPA2-PSK requires a Wi-Fi password ranging from 8 to 63 characters to encrypt the network traffic further. As WAP’s encryption technique is more robust, deciphering transmitted data is extremely challenging as the intruder has kept trying trial and error method.
However, the security of PSK is slightly flaky as everyone uses the same password; in case the password is distributed freely, it will hamper the security of all the users. On the contrary, the usage of passwords also leaves the system open to multiple attacks.
In case there is a password leakage, the tiring roll-out of updated passphrases follows. Moreover, Bruce-force attacks may be used to decipher the passcode.
What is a layer 2 Attack?
Open system Interconnection (OSI) paradigm layers are at ceaseless contact. The network’s physical layer or layer 2 is responsible for operational data movement between the devices. It transmits the raw data from the physical layer to the network layer. Disabling the network to harvest critical information poses a severe security concern in the layer 2 domain. Unfortunately, the crucial information have the lowest possibilities of being discovered.
- Here are few Layer 2 attacks that can take place on the network:
- Spoofing of ARP (Address Resolution Protocol)
- Spoofing of Media Access Control (MAC)
- A double tagging
- Spoofing of DHCP of Dynamic Host Configuration
- STP (Spanning tree protocol) attack
- Switch Spoofing
Example for PSK Network attack.
Consider a scenario where an organization has only WPA2-PSK for network security. Then the drawback is from receptionist to CEO will use the same password to access the company’s network. What concerns will it lead to?
Utilizing the passphrase becomes complicated when an insider threat exists; it can be a discontented employee who hacks into other devices on the company network or a malicious outsider who gains access to the organization’s internet to steal sensitive information. These foreign intruders can even inflict more harmful damages, such as financial loss, when WPA2-PSK is hacked.
Which is Better, AES Vs TKIP?
TKIP is a previously used encryption standard, which was the WPA standard. AES is the newer Wi-Fi encryption solution being used by the new-and-secure WPA2 standard. This is the theoretical approach of the scenario. However, choosing WPA2, depending on the router, is not good enough.
WPA2 is supposed to use AES for optimal security, but under specific scenarios, WPA2 might use TKIP. It’s only for cases where backward compatibility with legacy devices is needed. In such a state, devices that support WPA will connect with WPA; similarly, devices that support WPA2 will connect with WPA2, which is why WPA2 doesn’t necessarily mean WPA2-AES. Still, under circumstances when devices don’t show the option of “TKIP” or “AES”, it usually refers to WPA2-AES.
Wi-Fi Protected Access-Enterprise or WPA2-ENT
This is considered the gold standard for wireless network security protocol. WAP2 Enterprise always verifies the user’s server authentication services. Followed by it uses a 128-bit encryption key and dynamic session key to protect sensitive corporate information and wireless networks. Furthermore, it follows an authentication type aligned with the authentication protocol used by the 802.1X server.
WAP2-ENT technique to safeguard data by making password authentication possible through digital certificates. Digital certificates stop middle-man attacks from intercepting crucial information, such as credentials. Therefore, hackers cannot steal the password and use other resources.
The best part is that these authentication techniques apply to wired networks, and VLANS can be dynamically allocated. It also enables additional security to support network access protection (NAP).
How Does WPA2-Enterprise Work?
Serves are necessary for implementing WPA2-Enterprise as they authenticate users gaining access to a network. The authentication process involves 802.1X policy as its foundation and makes it available in several different systems that have been dubbed EAP. After each device has been confirmed, an encrypted tunnel is used to link the network.
To authenticate, WPA2-Enterprise requires to utilize secure EAP mechanism, EAP-TTLS/PAP, PEAP-MSCHAPv3 and EAP-TLS are the most often used. It has the capacity to accept a broad range of identities and enable MFA for more secure authentication.
Certificate-Based Security for WPA2-Enterprise:
When an organization utilizes a certificate for authentication, it simplifies the process for the user. A reset policy is not required. During certificate verifications, users are given temporary verified network access
EAP-TLS eliminates the chances of on-air credential theft; that’s why it is the most secured EPA protocol
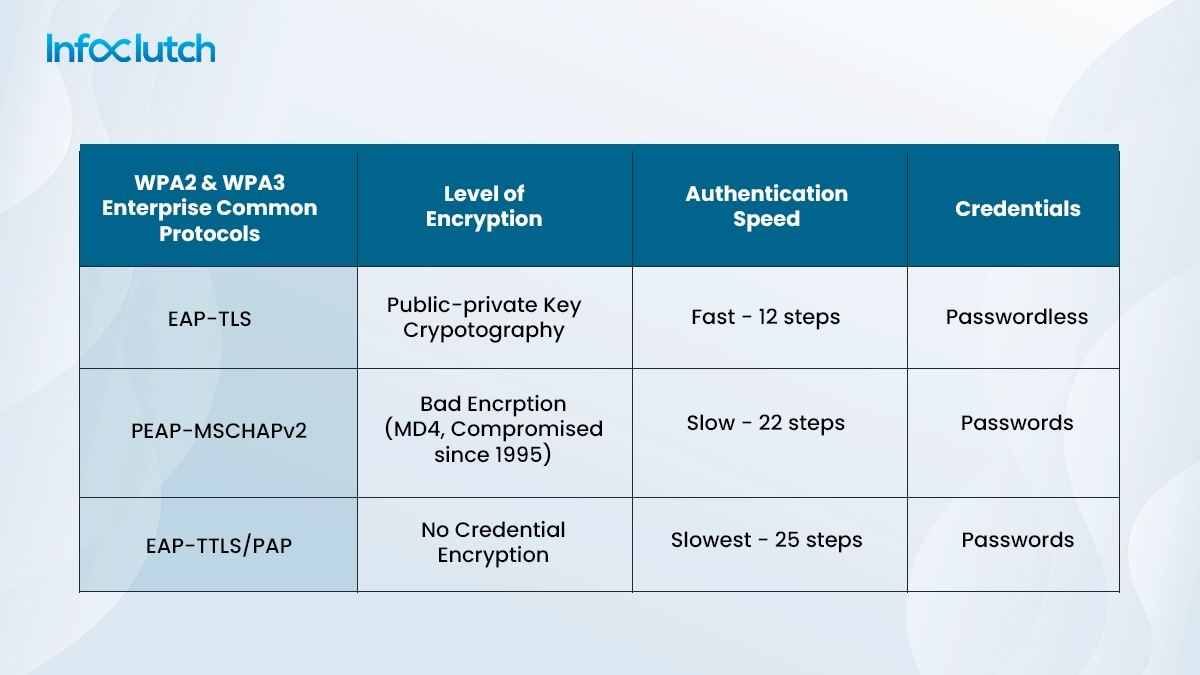
This covers the two different types of WPA2.
What is WPA3?
The third iteration of the Wi-Fi Protected Access Protocol is WPA3. It was introduced in 2018. It has features for both enterprise and personal use.
- Individualized Data Encryption: When you log into the new device, it signs you up through a process other than a shared password. It uses Wi-Fi Device Provisioning Protocol (DPP), which is basically using QR codes and (NFC) tags to add devices to the network. Furthermore, 128-bit encryption is not utilized; GCMP-256 is used for WPA3 security.
- Better Brute Force Assault Protection: WPA3 protects from offline password guesses, as the users are allowed only one guess. This means the users are forced to interact with the Wi-Fi device directly; hence, they have to be physically present every time there is a need to guess the password. WPA2 doesn’t have built-in encryption and privacy for public open networks, making brute force attacks a significant threat.
- Concurrent Authentication of Equal Protocols: The network device will establish a connection with the wireless access point to verify authentication and connection. Even in scenarios where the Wi-Fi password is weak, WPA3 provides a secure connection with Wi-Fi DPP.
Conclusion:
It is understandable that different types of WPA2 had a good run for providing security, but now WPA3 shows the highest security amongst all of them. Specifically when enterprise networks and public areas are taken into consideration. With more time passing by, new wireless security flaws will be discovered, and newer solutions will be needed to overcome those shortcomings for WPA3. However, WPA3 is the finest new wireless security protocol that protects no other. Using the WPA3 security will future-proof your wireless network.
In the business of promoting products and services to network security software providers, you landed at the right place at the right time. Contact our experts today to get a list of network security clients.










